Rekord
Solutions
The Industry Challenge
Enterprise IT teams face an impossible situation: prove what happened during security incidents when attackers specifically target logs and evidence.
THE CRITICAL FAILURES
- 85% of security incidents involve log tampering by attackers
- $4.45M average breach cost increased by inability to prove timeline
- Legal liability from inability to demonstrate due diligence
- Compliance failures when audit trails are compromised
Why Current Solutions Get Hacked
Standard logs can be deleted or modified. SIEM systems rely on the same compromised infrastructure. When everything is infected, how do you prove what really happened?
Traditional vs. Rekord Approach
What You Need
Tamper Protection
Incident Response
Breach Investigation
Compliance Auditing
Legal Evidence
traditional systems
Database logs (easily modified)
6 weeks of forensic analysis
18-month legal proceedings
“Trust us” explanations
Questionable in court
rekord
Mathematical impossibility
6-minute automated reports
48-hour mathematical proof
Independent verification
Cryptographic certainty
How It Works for Agriculture
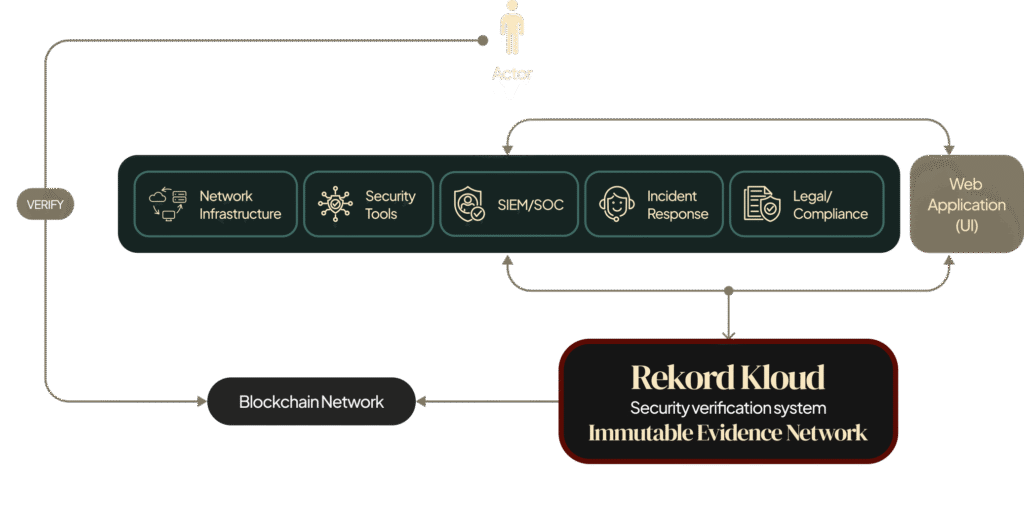
Connect
Integrate with your existing SIEM, endpoint detection, and security orchestration platforms in minutes.
Publish
Every security event, incident response action, and compliance control gets mathematical verification the moment it occurs.
Link
Share cryptographic proof with insurers, regulators, and legal teams without exposing sensitive security details.
Verify
Real-time dashboard shows verification status, compliance metrics, and incident response readiness.
Monitor with Rekord Kloud
Connect related security events across multiple systems while maintaining complete audit trails.
Create Transparency
Generate immutable security trails that auditors can verify independently without accessing your systems.
Specific features that matter most
Blockchain-Based Verification Built for agricultural operations
Every component specification, quality test, and assembly record receives cryptographic fingerprinting that creates mathematical impossibility of unauthorized changes.
Food Safety Automation FDA, USDA, HACCP ready
Automated quality reporting with mathematical proof of compliance. Turn months of quality documentation into minutes.
Transparency Verify without exposing
Share cryptographic proof with auditors and insurers without revealing sensitive security architecture or incident details.
Trust Mathematical certainty over hope
Transform product liability investigations into mathematical proof. When failures happen, provide evidence, not explanations.






